What Every Small Service Provider Needs to Know About Mitigating Illegal Robocalls with SHAKEN
The Signature-based Handling of Asserted information using toKENs (SHAKEN) framework is a foundational element to help minimize the illegal robocalls, scams, and Caller ID spoofing that over 90 percent of U.S. adults say are “annoying” and “disruptive.” SHAKEN gives service providers the tools needed to sign and verify calling party information, which can help trace these calls and stop them at their source. It also makes it possible for consumers to know—before answering—that the calls they receive are from a legitimate party.
SHAKEN has extensive industry support. The Alliance for Telecommunications Industry Solutions (ATIS) worked with the SIP Forum to develop SHAKEN. The framework uses Secure Telephone Identity Revisited (STIR) standards, which Internet Engineering Task Force (IETF) developed.Smaller service providers that are preparing for SHAKEN now will help lead the charge on the industrywide effort to relieve customers who are fed up with illegal robocalls and caller ID spoofing. Those that lag may find their subscribers in a much more focused audience that remains vulnerable to these spam and scam calls.
Understanding the Ecosystem
When developing SHAKEN implementation plans, service providers can use the following diagram to identify the key components and specifications.
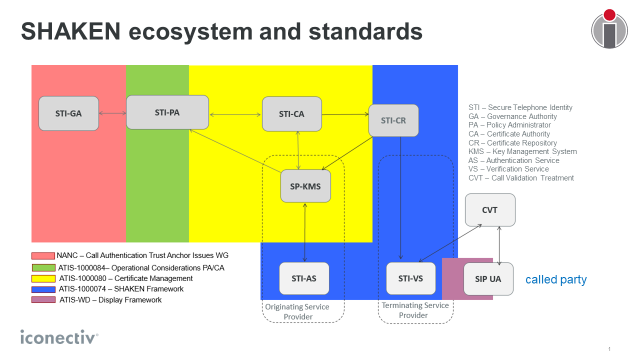
The Secure Telephone Identity Governance Authority (STI-GA) is an industry body that defines the rules to ensure that only eligible service providers and certificate authorities (CAs) are participating in the SHAKEN framework. Several mobile service providers are among the STI-GA leadership, including CCA members NEX-TECH Wireless and T-Mobile.
The STI-GA entrusts iconectiv, the nation’s Secure Telephone Identity Policy Administrator (STI-PA), to enforce SHAKEN rules, which specify a mechanism to ensure trust when service providers authenticate calling party information. Among its responsibilities, the STI-PA confirms which service providers are authorized to request STI certificates and reviews and approves STI-CAs that issue them.
With this policy administration in place, calling party information such as the origination of the call and the Caller ID finally can be authenticated. SHAKEN will capture this information for each call and securely will convey it to the called party’s service provider.
To support SHAKEN, service providers need to add several capabilities, including:
• A key management system (KMS) in their back office to house their private key and the authority token provided by the STI-PA to use with CAs. This system interfaces with the CA to request certificates in a secure manner.
• An authentication service (AS) that handles the signing process when originating calls. The AS determines whether there’s a verified association between the phone number and the customer using that number. The AS also assigns a unique origination identifier in the header for trace back, which is among the ways that the SHAKEN framework identifies and weeds out illegal robocalls.
• A verification service (VS) that handles the analysis of the signed calling party information using the public key certificate provided by the originating service provider. This information is checked for tampering using the signature and is provided to the Call Validation Treatment (CVT) module.
• The CVT provides call blocking and display decisions using a variety of data sources including the information provided by SHAKEN.
All of these components will make a significant difference in reducing illegal robocalls; both in terms of the information that might be used to decide to block calls, as well as the information that called parties receive about calls that are not blocked. This information empowers consumers to decide whether to answer a call, let it go to voicemail, or use their handset’s client app to add the number to their personal blocked list.
